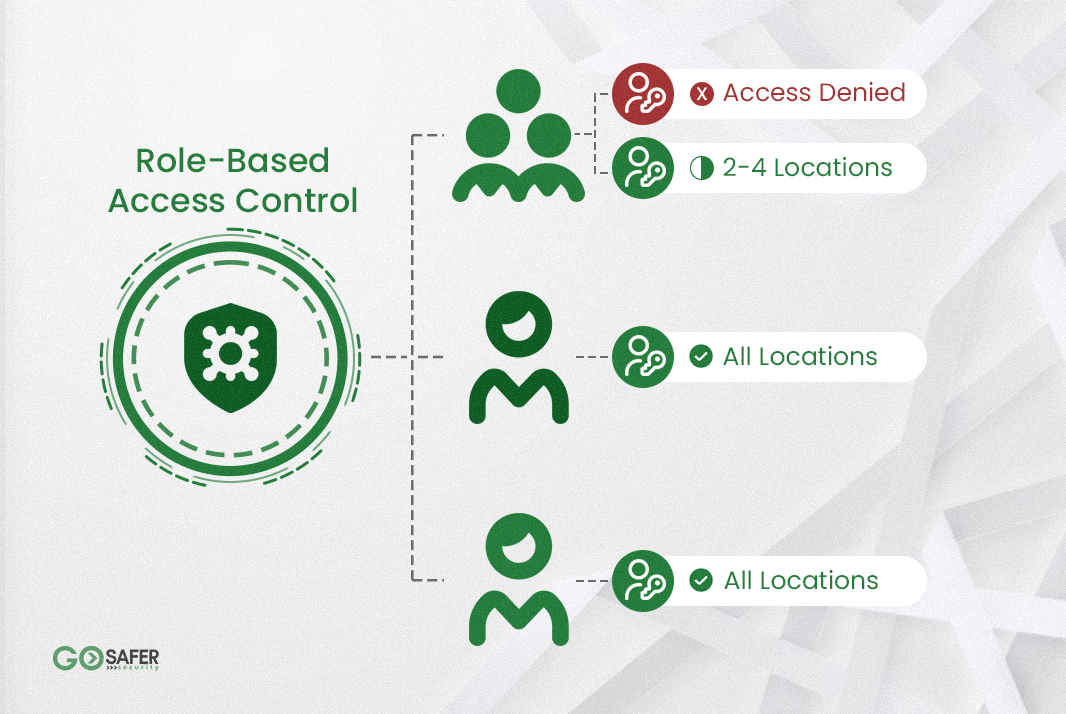
Managing who has access to sensitive information and critical areas is essential for any organization. Role-Based Access Control (RBAC) is a security framework that assigns permissions based on roles within a company, ensuring that only authorized users can access specific systems, data, or locations.
Whether you’re securing an IT network or managing a physical access control system, understanding RBAC is key to enhancing security while maintaining efficiency. This guide breaks down how RBAC works, its benefits, and how to implement it for your business.
Table of Contents
ToggleWhat Is Role-Based Access Control (RBAC)?
RBAC is a method of restricting access based on the roles assigned to users within an organization. Instead of granting permissions on an individual basis, access is granted according to a user’s role. This approach:
✔ Ensures employees only access the data and systems necessary for their jobs.
✔ Reduces security risks by preventing unauthorized access.
✔ Simplifies access control system installation and management.
For example, in a hospital, doctors may have access to patient records, but receptionists may only access appointment schedules.
How Does Role-Based Access Control (RBAC) Work?
RBAC operates using three core components:
1. Roles
A role is a predefined set of permissions assigned to users based on their job responsibilities. Examples include:
- Administrator: Full system access.
- Manager: Access to employee records but restricted from financial data.
- Employee: Limited access to work-related applications.
2. Permissions
Permissions define what a role can do within a system, such as:
- Reading or modifying data.
- Viewing confidential reports.
- Entering restricted physical areas.
3. Users
Each user is assigned a role that dictates their access level. Instead of managing individual permissions, administrators simply assign or remove roles as needed.
Key Benefits of Role-Based Access Control (RBAC)
1. Improved Security
By restricting access to sensitive data and locations, RBAC prevents unauthorized users from obtaining critical information or entering restricted areas.
2. Simplified Access Management
RBAC reduces administrative workload. Instead of assigning permissions to each user, roles are managed at a higher level, making access control system installation and configuration easier.
3. Compliance with Security Regulations
RBAC helps businesses comply with industry regulations like HIPAA (for healthcare) and GDPR (for data privacy) by ensuring data is only accessed by authorized personnel.
4. Reduced Risk of Human Error
Manually assigning access can lead to mistakes. RBAC minimizes human error by enforcing consistent security policies.
5. Increased Efficiency
With predefined roles, employees gain instant access to necessary tools and data, reducing downtime and increasing productivity.
Implementing RBAC in Your Access Control System
To successfully integrate RBAC, follow these steps:
Step 1: Identify Roles & Responsibilities
Determine which roles exist within your organization and what permissions they require. Consider:
- Who needs access to sensitive files?
- Which employees require physical entry to certain areas?
Step 2: Define Access Rules
Set up clear policies for each role, specifying:
- Data access restrictions.
- Physical entry permissions.
- Privileges for system changes.
Step 3: Install an Access Control System
A secure access control system installation ensures that RBAC policies are enforced efficiently. Systems may include:
- Keycard or biometric access control for physical security.
- Identity and access management (IAM) software for digital security.
Step 4: Assign Roles to Users
Once your system is in place, assign roles to users based on their job requirements.
Step 5: Regularly Audit Access Permissions
Review access logs and permissions regularly to:
✔ Revoke unnecessary access.
✔ Identify potential security risks.
✔ Ensure compliance with security policies.
RBAC vs. Other Access Control Models
| Access Control Model | Description | Best For |
| RBAC (Role-Based Access Control) | Assigns access based on predefined roles. | Organizations with structured roles. |
| MAC (Mandatory Access Control) | Access is granted based on security clearances. | Government and military environments. |
| DAC (Discretionary Access Control) | Users have control over their own access permissions. | Small businesses with minimal security needs. |
RBAC strikes a balance between security and flexibility, making it ideal for businesses, healthcare, and IT security.
Common Challenges in RBAC Implementation
1. Over-Complicating Roles
Solution: Keep role definitions simple and limit the number of role variations.
2. Failure to Update Permissions
Solution: Conduct regular access audits to ensure employees only have necessary access.
3. Lack of Employee Awareness
Solution: Train employees on the importance of access control and security best practices.
Frequently Asked Questions (FAQs)
1. How does RBAC improve cybersecurity?
RBAC limits access to critical data and systems, reducing the risk of cyberattacks by unauthorized users.
2. Can RBAC be used for physical security?
Yes, RBAC can restrict access to physical locations using keycard or biometric access control systems.
3. What industries benefit most from RBAC?
Healthcare, finance, IT, and corporate offices benefit the most due to strict security and compliance requirements.
4. How often should businesses review RBAC permissions?
Regular reviews, at least every 6 months, help prevent unauthorized access and ensure compliance.
5. Can small businesses use RBAC?
Yes! Even small businesses benefit from RBAC by improving security and streamlining user access.
Conclusion
Role-Based Access Control (RBAC) is a powerful tool for managing access efficiently while enhancing security. Whether you’re securing digital data or physical spaces, RBAC ensures that only authorized personnel have the right level of access.
By implementing RBAC within an access control system, businesses can reduce security risks, simplify user management, and comply with industry regulations.
Start improving your access control today by evaluating roles within your organization and investing in a reliable access control system installation.